For the Beijing 2022 Winter Olympics, the Chinese government requires everyone to download an app onto their phone. It has many security/privacy concerns, as CitizenLab documents. However, another researcher goes further, claiming his analysis proves the app is recording all audio all the time. His analysis is fraudulent. He shows a lot of technical content that looks plausible, but nowhere does he show anything that substantiates his claims.
Average techies may not be able to see this. It all looks technical. Therefore, I thought I'd describe one example of the problems with this data -- something the average techie can recognize.
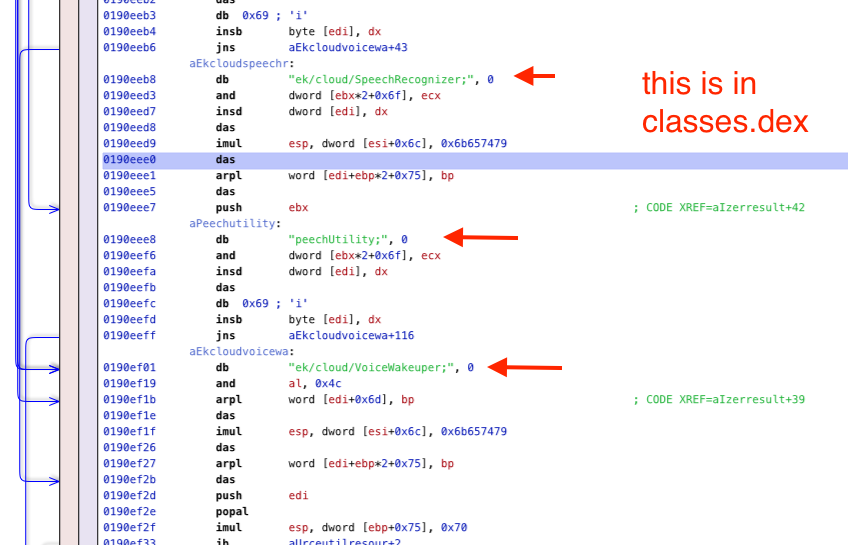
His "evidence" consists screenshots from reverse-engineering tools, with red arrows pointing to the suspicious bits. An example of one of these screenshots is this on:
It fails the sniff test. Different researchers will notice different things first. Famed google researcher Tavis Ormandy points out one flaw. In this post, I describe what jumps out first to me. That would be the 'imul' (multiplication) instruction shown in the blowup below:
It's obviously ASCII. In other words, it's a series of bytes. The tool has tried to interpret these bytes as Intel x86 instructions (like 'and', 'insd', 'das', 'imul', etc.). But it's obviously not Intel x86, because those instructions make no sense.
That 'imul' instruction is multiplying something by the (hex) number 0x6b657479. That doesn't look like a number -- it looks like four lower-case ASCII letters. ASCII lower-case letters are in the range 0x61 through 0x7A, so it's not the single 4-byte number 0x6b657479 but the 4 individual bytes 6b 65 74 79, which map to the ASCII letters 'k', 'e', 't', 'y' (actually, because "little-endian", reverse order, so "ytek").
No, no. Techies aren't expected to be able to read hex this way. Instead, we are expected to recognize what's going on. I just used a random website to interpret hex bytes as ASCII.
There are 26 lower case letters, roughly 10% of the 256 possible values for a byte. Thus, the chance that a random 4 byte number will consist of all lower-case letters is 1-in-10,000. Moreover, multiplication by strange constants happens even more rarely. You'll commonly see multiplications by small numbers like 48, or large well-formed numbers like 0x1000000. You pretty much never see multiplication by a number like 0x6b657479, baring something rare like an LCG.
QED: this isn't actually an Intel x86 imul instruction, it's ASCII text that the tool has tried to interpret as x86 instructions.
Conclusion
At first glance, all those screenshots by the researcher look very technical, which many will assume supports his claims. But when we actually look at them, none of them support his claims. Instead, it's all just handwaving nonsense. It's clear the researchers doesn't understand them, either.

2 comments:
Thank you for sharing useful information with us. please keep sharing like this. And if you are searching a unique and Top University in India, Colleges discovery platform, which connects students or working professionals with Universities/colleges, at the same time offering information about colleges, courses, entrance exam details, admission notifications, scholarships, and all related topics. Please visit below links:
Mahakaushal University in Jabalpur
YBN University in Ranchi
Manipal University Jaipur
Swami Vivekanand University in Sagar
No need to force country people for a using app like this, its all about people choice. Please check more about Affordable marketing agency, Rough Terrain Crane, rough terrain crane rental
Post a Comment